"Just Show Me the Risk First" - Why This Common Executive Push-Back Misses the Point
I hear it regularly in boardrooms across Europe: "We should only implement controls if we can demonstrate a specific risk that justifies them." On the surface, it sounds rational. Risk-based decision making is, after all, best practice. But this objection reveals a fundamental misunderstanding of how cybersecurity actually works—and it can leave organizations dangerously exposed.
The Three-Layer Reality
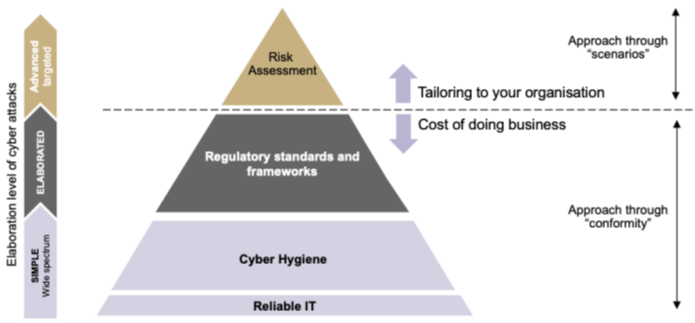
Recent research from Antwerp Management School (Verslegers & Bobbert, 2024) provides the evidence-based framework I've been needing to counter this argument. Their "Cybersecurity Investment Pyramid" makes explicit what many of us have known intuitively: not all security controls belong in the same decision-making category.
Their pyramid has three distinct layers:
1. Cyber Hygiene (Base Layer) This is the non-negotiable foundation. Multi-factor authentication. Patch management. Asset inventory. Proper authentication and authorization. Logging. Basic hardening.
These aren't optional investments waiting for a risk assessment—they're the cost of operating digitally, period. As the AMS research shows, breach analyses consistently demonstrate that failures in these basic controls (lateral movement, overprivileged users, configuration errors) are the dominant root causes of incidents.
2. Compliance (Middle Layer) Regulatory requirements like NIS2, DORA, GDPR Article 32, or ISO 27001. These are your ticket to operate in specific markets or sectors. The decision here isn't whether to implement them, but how cost-effectively you can do so while meeting the standard.
3. Risk-Based Controls (Top Layer) Only here—after you've built the foundation and met compliance requirements—should you be running detailed risk scenarios and ROSI calculations for additional, organization-specific controls.
Figure 1: Different contexts for security investment decisions
Why This Matters in Practice
When executives demand risk justification for everything, they're essentially asking: "Prove to me that someone will attack us before we lock the doors."
That's backwards. As the AMS research demonstrates, organizations with "thin" compliance layers need to address far more threats through expensive, bespoke risk analysis. Those with solid hygiene and compliance foundations can focus their advanced risk modeling on the scenarios that actually matter to their specific business.
A Real-World Example
Let me share a situation that illustrates this perfectly. A client operates as a remote-first company but maintains a small office space within their parent company's building. The parent company has turnstiles and badge controls at the building entrance.
A laptop went missing. Not stolen—just missing.
When we documented the risk ("No lock installed on [Company]'s office"), the management response was essentially: "Well, the building has security, so this isn't really a problem. Show us why we need a lock on our specific office door."
This is the "show me the risk first" fallacy in action. The risk register shows the issue. A laptop already went missing. Yet because the parent company has perimeter security, management views an office door lock as optional—something requiring additional risk justification.
But here's the reality: a lock on your office door is cyber hygiene, not a risk-based control. It's part of physical security basics, like having asset inventory, visitor logs, or clean desk policies. You don't quantify the Annual Loss Expectancy of someone walking into an unlocked room during business hours. You just lock the door.
The building's turnstiles control who enters the building. They don't control who accesses your company's space within it—employees of the parent company, contractors, visitors, cleaning staff. All can access the shared corridors. Without a lock, you're treating your office like a public space.
This isn't about sophisticated threat modeling. It's about implementing basic physical security controls that any organization handling sensitive data should have—regardless of whether you can prove someone will exploit the gap.
The irony? They'll likely spend more time in meetings debating whether they need the lock than the lock would cost to install.
The Right Question
Instead of "show me the risk first," the better executive question is: "Which layer of the pyramid are we discussing?"
Hygiene controls? Don't justify, just implement efficiently. Focus on total cost of ownership and technical fit.
Compliance controls? Quantify the cost of non-compliance (fines, lost business opportunities) vs. implementation cost.
Risk-based controls? Now we break out the scenario analysis, Annual Loss Expectancy calculations, and ROSI models.
My Take
The "risk-based everything" mentality sounds sophisticated but often masks an unwillingness to invest in fundamentals. I've seen organizations spend €50k on penetration testing while running without MFA or proper logging—essentially paying consultants to tell them their house is on fire while refusing to buy smoke detectors.
The AMS framework gives us the language to have more productive conversations: cybersecurity investment is context-dependent. Different contexts require different justification approaches. Risk quantification is powerful and necessary—but only after you've addressed the basics that every organization needs regardless of their specific threat landscape.
Bottom line: If your management team is demanding risk analysis before implementing cyber hygiene basics, you're not being rigorous—you're being penny-wise and pound-foolish.
Reference: Verslegers, D., & Bobbert, Y. (2024). From Gut Feel to Gains: The Cybersecurity ROI Pyramid. Antwerp Management School. https://www.antwerpmanagementschool.be/en/blog/from-gut-feel-to-gains-the-cybersecurity-roi-pyramid